Hacktivist RIAEvangelist sparked outrage beyond the FOSS (Free and Open Source Software) community after uploading “protestware” (read malware) to his own repository
Brandon Nozaki Miller, going by the GitHub handle RIAEvangelist, is the creator and maintainer of widely-used ‘node-ipc’. And now author of ‘peacenotwar’, a recent module within ‘node-ipc’ which despite its name shamelessly engages in information warfare.
His software package is favoured by Javascript systems programmers for its efficiency. Which sounds a little too distant to reside amongst our everyday worries, right?
But ‘node-ipc’ in turn gets incorporated downstream into major libraries – like popular web framework ‘Vue.js’. The latter received over 3 million downloads during this week alone.
Such open-source projects form the backbone of mainstream computing systems today. Hence, we should be extremely concerned about the wider implications of software maintainers abusing their rights.
How it unfolded
RIAEvangelist’s intentions were straightforward: delete all files on computers whose IP hailed from Belarus or Russia. Replace those files with ❤️emojis and end the war. Case closed.
Be that as it may, it is worth noting military targets probably remain unaffected. Defence sectors place stringent guidelines on air-tight networks by design. So who were the true recipients of his love?
While I sympathise with his “good” malware wrecking havoc on malicious warmongers, the collateral victims didn’t deserve this indiscriminate punishment. What say did the average developer residing in those countries have pertaining to the invasion of Ukraine? To say nothing of how capricious geolocation identification via IP-tracking can get!
Crucially, a caveat with Javascript’s ‘npm’ package manager concerns how server-side ‘node.js’ software is currently installed. Running the high-level command ‘npm install’ entails hidden risks of running dependency packages unbeknownst to the average users. Unless they take the time to read and understand the source code of each and every package!
Burying The Evidence
The great thing about version control systems like ‘git’ is that all changes are tracked. And stay tracked, despite the hacktivist’s futile attempts to surreptitiously pull it down fearing backlash. After failing to cover his tracks via obfuscating the malware, he resorted to outright denial at first.
To add insult to injury, RIAEvangelist extended his antics by replacing his payload, instead bundling ‘WITH-LOVE-FROM-AMERICA.txt‘ in subsequent updates. Thus peppering infected Desktop environments with the more benign punishment of “peace” pop-ups.
Then came the post-justification power-move:
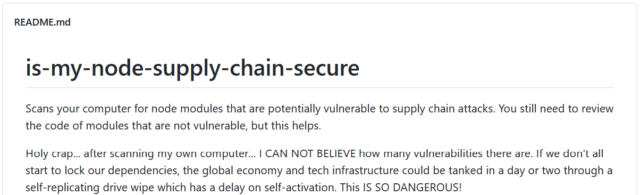
Screenshot of README extract from Miller’s latest software package (as of 31/03/22)
Not content with spreading thinnly-disguised malware masked in a message of peace and love, he’s ironically released a vulnerability-scanning program. It’s almost amusing to read his narrative of having wished to underscore our susceptibility to software supply chain attacks. A tad too late to restore community reputation points.
Wider implications
A likely fake, but nonetheless contextually significant account by an alleged NGO employee claimed the following:
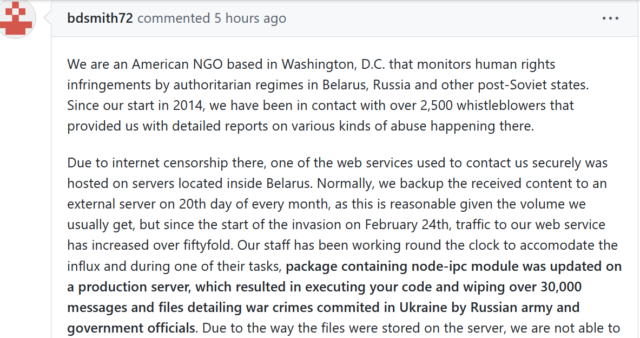
Screenshot of an as-yet-unverified NGO’s claim on ‘GitHub issue thread for ‘node-ipc’
In the resulting online flame war, RIAEvangelist continued to defend his protestware. He went as far as accusing the respective NGO of negligent file backups and opined they might be in violation of US data protection laws.
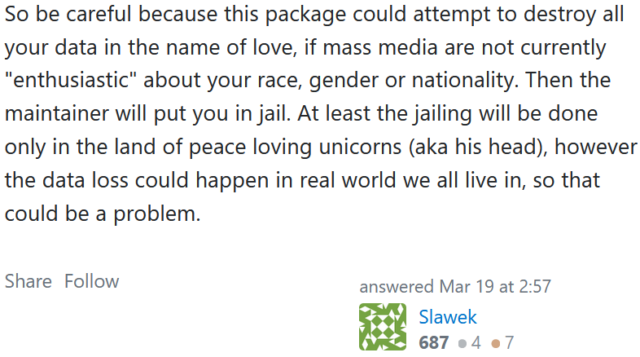
On Stack Overflow, an incensed user with a flair for the ridicule replied:
It’s a valid point: why the sudden upsurge in protestware evangelists?
Precedent For Freedom
Another appalling precedent dates back to January of this year. Marak, the maintainer of popular open-source libaries ‘colors’ and ‘faker’, stunned the FOSS community through his mischievous commits. Subsequently, three lines of ‘LIBERTY’ flooded users’ console displays, followed by gibberish printing of non-ascii characters.
Despite a forced exile from repository host GitHub, Marak received far more positive reviews than RIAEvangelist. Partly due to his motivation: a protest against mega-corporations taking open-source projects as their own without due credit. And chiefly because it didn’t obliterate someone’s work files, photos and everything in between.
“Respectfully, I am no longer going to support Fortune 500s (and other smaller sized companies) with my free work,” wrote the developer. “Take this as an opportunity to send me a six figure yearly contract or fork the project and have someone else work on it.”
That being said, it’s terrible taste to sabotage your own work. Moreover, extorting the billion-dollar companies he loathes is even more terrible taste. Any competent IT department would have locked and tested their builds during software updates. Consequently, another case of missing the target, hitting his supporters instead.
Positive Outcomes
Intent and extent of one’s spiteful disuptions are critical. Just as Tube strikes incite mixed feelings of praise and condemnation, carefully-executed protestware has potential to bring about political change.
Clearly, downloading the latest update isn’t so hip after all. From a security standpoint, RIAEvangelist successfully highlighted the importance of dependency pinning. This simply involved editing the patch control file to fetch independently-tested, safe versions at all times. As for Marak, dwindling appreciation for a handful of volunteers powering the software market was put back on spotlight.
The value of proactive code reviews has also been re-raised in community threads. FOSS developers have long touted global eyes hawk away malicious actors. Yet no-one, not even bots, can possibly trawl through and flag trillions of lines of code in real-time. The common myth that open-source trumps over proprietary closed-sourced software in security auditing is very much false. Both can be just as prone to vicious attacks. By the beloved creators themselves.
[Stay tuned next week for an extended review on the motivations driving millions of open-source projects worldwide.]